
Spread a little love (and laughter) in the security world. Download free, not-at-all-creepy Valentine’s Day cards made just for security...
You finally did it.
You set up Tailscale so you could access your Milestone XProtect system from anywhere without wrestling with VPN configs that feel like they were invented in the 1800s.
You pour yourself a coffee, open Smart Client, and prepare for the satisfaction of logging in securely from the comfort of your cabana.
And… nothing works.
Welcome to the moment every admin hates: the setup looks fine, but Milestone just won’t let you in.
Here’s what’s actually going on—and how to fix it.
Setting up Tailscale for Milestone XProtect gives you:
Secure access from anywhere
Whether you’re working from home, on vacation, or managing multiple sites, you get encrypted point-to-point access to your VMS.
No complicated VPN configs
Seriously. No firewall rule nightmares, port forwarding rituals, or asking IT to open a sacred portal in the network.
Single Sign-On with your IDP (if configured)
Which means one less password for your users and one more reason your CISO might smile.
Peace of mind
Once it works, it just works—from anywhere in the world.
But the key phrase here is: once it works.
Here’s the deal…
When you install Tailscale on your Milestone server, it gets a new internal IP from Tailscale’s magic mesh network. Great, right?
Except… Milestone doesn’t know what to do with that new IP.
So when Smart Client tries to connect over Tailscale, the server just kind of shrugs and ghosts you.
It’s not you. It’s not Tailscale.
It’s that Milestone doesn’t know how to respond to the traffic coming in over that unfamiliar subnet.
Add your Tailscale subnet to Milestone’s list of external addresses.
Why this works:
Milestone lets you define external IPs or subnets so it knows how to respond when clients connect from those networks.
By adding the Tailscale subnet to this list, you’re telling Milestone:
“Hey—if someone tries to log in from this range of addresses, reply using your own Tailscale IP.”
Basically, you’re giving the server the right return address to use when it gets traffic from the Tailscale side door.
Think of it like this:
Milestone is like a delivery guy.
You just added a new hidden alley entrance (Tailscale) to your building.
But unless you update the delivery instructions, he’s still trying to leave packages at the front door.
Adding the external address tells him:
“If someone buzzes from the alley, deliver the pizza to the fire escape.”
In Site Information, add the Tailscale IP to your list of alternate site addresses and check the External box.
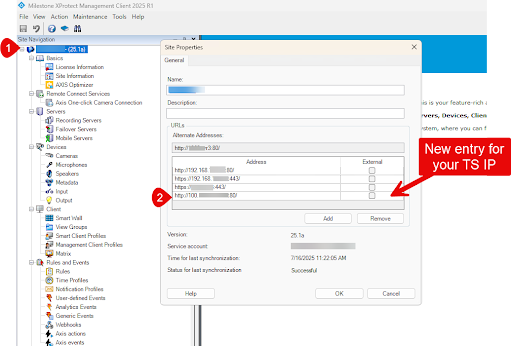
Add your Tailscale IP to the list of URLs under Gateway Services and mark it as External. Do all but the mobile server.
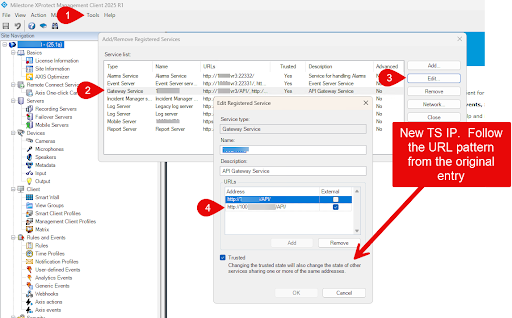
Head to Tools > Add/Remove Registered Services.
Select Gateway Service, then click Edit and follow the existing URL format to add your new TS IP (e.g., http://100…/API/).
Do this for all the services in the registered services list except for the mobile server.
Set your Tailscale IP as an external address with port 7563 in the Recording Server settings.
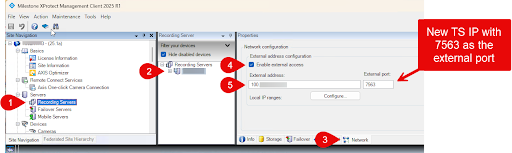
Open the Recording Servers section, select your server, and go to the Network tab.
Enable external access and add your Tailscale IP with the port 7563.
For the mobile server, you need to update your DNS record to point to the TS IP address vs the local IP address.
Milestone doesn’t know what to do with your Tailscale IP until you explicitly tell it how to respond.
Fix it by adding the Tailscale subnet to Milestone’s list of external addresses.
That way, your remote Smart Client sessions can connect securely and actually get a reply.
Remote access to Milestone shouldn’t feel like a trapdoor into network hell.
If you’re already using Tailscale, this small config tweak can make remote Milestone access feel frictionless—and way more secure.
Less frustration. More vacation.
Want more tips like this for managing your VMS without the headaches?
It’s the newsletter security professionals use to work smarter. We promise you’ll learn stuff and enjoy a few blissful moments of productive procrastination.

Your go-to XProtect eXPerts. We learn the technical stuff that will save you time and make it less boring.

Your go-to XProtect eXPerts. We learn the technical stuff that will save you time and make it less boring.

Spread a little love (and laughter) in the security world. Download free, not-at-all-creepy Valentine’s Day cards made just for security...

This blog introduces Analytics, a new feature in The Boring Toolbox that brings powerful trend visualization to Milestone XProtect. Learn...

Zipstream can dramatically reduce storage and bandwidth in Milestone, but only if it’s enabled correctly. This guide breaks down how...